The Cyber Conflict Portal (CCP) identifies six strands of politico-military uses of ICTs that can be considered incompatible with international peace, security and stability. The first iteration of the CCP examines individual effect-creating cyber operations, i.e. cyber operations that are publicly known to have resulted in changes in the targeted or affected system(s). Our next collections will focus on cyber campaigns, cyber offences targeted against public trust and the international community, cyber espionage, domestic cyber conflict and cybercrime associated with proxy actors and advanced persistent threats (APTs). This ontology of cyber conflict is intended to draw attention to trends and patterns in the use of ICTs for malicious and hostile purposes and to inform debates and discussions of how to best prevent and mitigate the various threads of politico-military use of ICTs.
Built on a wide and balanced reference base, CCP invites and promotes multi-disciplinary perspectives to cyber operations. Our database builds on earlier research on cyber conflict and complements the work done by the CFR, CSIS, Hackmageddon, and Dyadic Cyber Incident and Dispute Data. The database includes cross-references to ATT&CK and ICS analytical frameworks of the MITRE Corporation.
Effect-creating cyber operations
In an effort to facilitate research input into cyber diplomacy and policy processes, CCP adds special emphasis on the causes and enablers of cyber conflict, in order to allow technical, political and legal opportunities and gaps in cybersecurity preparedness to be identified and addressed. In addition to coded data, the database contains extensive factsheets detailing the context, enablers and implications of incidents.
Since 2007, on more than 20 occasions, states or state-sponsored actors have inflicted damage on another state using ICTs. While often such damages are relatively benign, such as downtime of public services or inaccessible information on a website, several incidents have resulted in significant economic damages or affected critical services. Effects of cyber operations often include manipulation, disruption and destruction of data.
Each dot represents a separate cyber operations. Hover and click on the dots for detailed information and to access an operation’s factsheet.
Targeted sectors
The financial sector is most affected by state-sponsored cyber operations. Cyber operations also disrupt manufacturing processes, and interrupt the supply of electricity and public transportation. State-sponsored cyber operations have disrupted fuel supply and targeted nuclear facilities.
Ongoing military conflicts
Unlike other military operations, hostile uses of ICTs mostly occur outside acute military conflict. Cyberspace facilitates low-intensity conflict between nuclear powers and allows operational presence away from the operating state’s territory. Most states engaging in cyber operations have established a cyber command.
Dyads
Scholars have noted the dyadic nature of cyber conflict – in most instances, cyber operations are situated in pre-existing political tensions. However, for some states, ICTs offer a firsthand opportunity to engage in operations against their rivals.
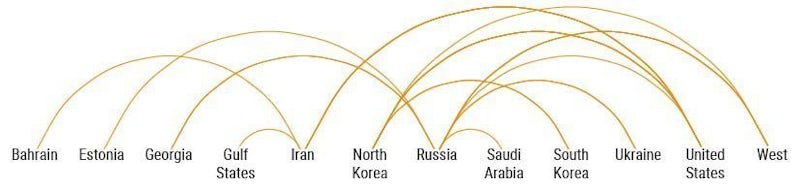
Proxies
International cyber diplomats and scholars are concerned with the engagement of non-state actors in cyber operations. Our research indicates that even states with established cyber commands rely on proxy actors when carrying out cyber operations.
Processes and dialogues
Global and regional cybersecurity dialogues are led by states that also use ICTs to support their domestic, regional and global ambitions. At the same time, these dialogues do not comprise all countries frequently engaging in cyber operations.